Many times the companies need give access to external users (i.e. suppliers) to their own Intranet or Extranet application. The best solution in this case is not create users on the internal domain controller but use another alternative repository for store and manage the identities in order for maintain distinct the two worlds. In view of this you can:
- Create another domain controller
- Setup FBA (Form Based Authentication)
- Use an external provider like Azure Active Directory
Leaving the first point because I think that is not an elegant solution, usually I suggest to implement FBA because it is easy and it is quickly configurable on SharePoint but lately, if you have an subscription on Windows Azure, I encourage use Azure Active Directory through Access Control Namespace because it is on the cloud and opens many potential scenarios like give the possibility login with Google or Facebook Account.
I don’t want to write how to configure SharePoint with Azure AD because it is well explain on the TechNet article but I carry-over only the two differences that I done to permit to run the service correctly :
- I didn’t create Azure AD Tenant Namespace but I created a new application under the my Azure Domain and I set Document Federation Metadata endpoint as URL Identity Provider;
- I changed the lifetime of the SharePoint token without which I had a loop authentication between SharePoint and Azure. For this purpose I ran this PowerShell script:
$sts = Get-SPSecurityTokenServiceConfig $sts.LogonTokenCacheExpirationWindow = (New-TimeSpan -minutes 1) $sts.Update() iisreset
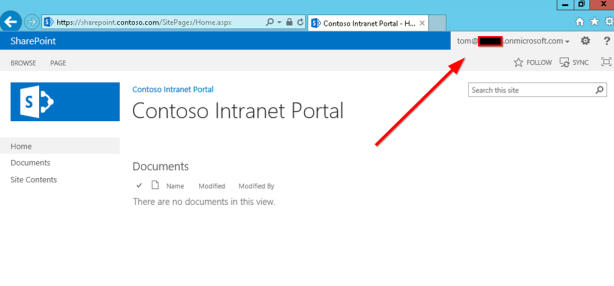
Below you can see the my final result after I finished all setup:
- On Azure AD I create a new user account

- I give permission to access on SharePoint
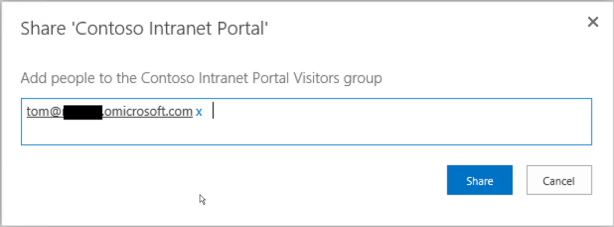
- I try access on SharePoint with Azure user account (tom@xxxx.onmicrosoft.com) but given that it’s the first access, user must change the temporary password

- After login on Azure portal I am redirect on my SharePoint
Some Considerations
- I suggest do not use more than one authentication providers on same SharePoint zone because this solution implicate that user must select the correct provider during login operation
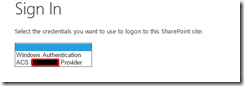
- If you can’t login for some issue, investigate with SharePoint logs
- SharePoint People Picker can not resolve users on SAML authentication provider, to solve this inconvenience you can install a solution that fix this issue. An example is https://github.com/Yvand/AzureCP
Conclusion
I hope that with this post you can quickly implement Azure Active Directory authentication on your SharePoint and begin leverage the Cloud.
Simone F.